 For IT administrators, remote access to all of their machines reduces the time and effort spent on urgent fixes and provides peace-of-mind in the case of emergencies or major issues.
For IT administrators, remote access to all of their machines reduces the time and effort spent on urgent fixes and provides peace-of-mind in the case of emergencies or major issues. 
The nature of edge deployments means that they are always on, sometimes running 24/7 in a different time zone than the IT administrators. So when a system experiences a bug or major issue, IT is required to travel to the edge site and debug the system. Sometimes this happens in the middle of the night. Even when teams have the foresight to set up tools in place to allow for remote access, they are often costly to develop, difficult to use, and present significant security vulnerabilities.
For IT administrators, remote access to all of their machines reduces the time and effort spent on urgent fixes and provides peace-of-mind in the case of emergencies or major issues. While versions of this tool can be found in other products, many lack critical features that are becoming increasingly important for organizations deploying and scaling AI at the edge. One of them is security.
To solve this, Fleet Command includes on-demand remote console functionality available to all administrators. Recently, we added several new features to remote console to increase security and to allow users to concurrently access multiple edge nodes in an organization.
Remote console is a mechanism allowing the Fleet Command administrator to securely access NVIDIA-Certified systems at edge locations, ensuring proper authorization and authentication mechanism. It provides remote access to allow administrators to streamline troubleshooting and emergency management from the comfort of their office.
Secure access at the edge
The most difficult part of building remote console functionality is ensuring the right security protocols are in place to prevent vulnerabilities and to restrict malicious behavior. Major security breaches have occurred through perpetually open VPN instances that were created so IT administrators could remote access systems at other locations.
Today, IT teams are left with the difficult choice of spending resources to meticulously develop their own security protocols or to operate remote console sessions with little or no protection in place. With Fleet Command, IT teams no longer need to make that choice.
Remote console on Fleet Command is secure by default. It gives the Fleet Command administrator an on-demand browser-based shell to edge nodes using an ephemeral reverse websocket tunnel. Additionally remote console uses the standard TLS port 443 and does not require customers to open custom ingress firewall rules in their network, reducing the complexity of getting started.
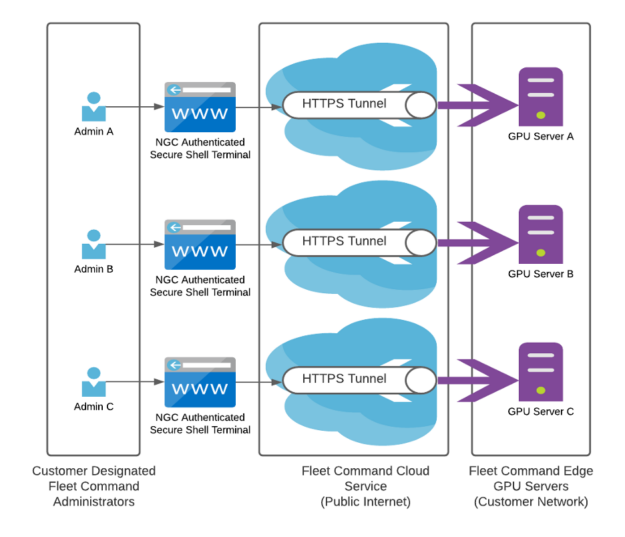
Since SSH access is granted through broker/remove with temporary elevation with a 1 hour default timeout, as opposed to standing access, remote console through Fleet Command provides just-in-time (JIT) access. JIT access helps minimize the risk of standing privileges that can be exploited by malicious actors.
Without JIT security, users are effectively given unlimited, privileged access to the systems at edge locations and the data and resources on them. By limiting the window of access with remote console on Fleet Command, organizations significantly reduce the risk of exposure.
Simultaneous fleet wide access
Another unique aspect of remote console on Fleet Command is usability. Because Fleet Command is a turnkey solution, all tools and features are designed to be as straightforward and easy to use as possible. One of those features, multiple remote console, allows for concurrent access to multiple edge nodes in an organization. By giving administrators access to multiple locations at the same time, they are able to provide simultaneous troubleshooting capabilities across their entire edge fleet. Multiple remote console allows access to one or many locations, and even has the ability to collaborate with other administrators.
To ensure the highest security across nodes, Fleet Command infrastructure isolates each of the open nodes on multiple remote console and ensures any issues on one of the systems does not affect other sessions.
Using remote console on Fleet Command
Using remote console on Fleet Command takes only a few clicks and is available through the Fleet Command user interface.
New features are constantly added to Fleet Command to give organizations access to immediate innovation. The philosophy behind building a turnkey solution means that every new feature added is one feature that does not need to be built or designed by your developers. This accelerates the time it takes for you to go from zero to AI. Purpose-built for AI, Fleet Command includes dozens of these features and functionality that make new opportunities and use cases possible for virtually every industry.
Get started on Fleet Command
Getting started on Fleet Command is easy and trials are available on NVIDIA LaunchPad for any organization to evaluate the value of quickly deploying AI at scale. The NVIDIA LaunchPad program enables quick testing and prototyping on the same complete stack you can purchase and deploy.
With Fleet Command on LaunchPad, organizations get access to:
- a turnkey cloud service to easily deploy and monitor real applications on real servers
- a catalog of models and applications to explore the benefits of AI
- an accelerated edge computing infrastructure from Equinix to seamlessly provision and run applications
View Fleet Command features in action.
