 Developing a high-performing Hebrew large language model (LLM) presents distinct challenges stemming from the rich and complex nature of the Hebrew language…
Developing a high-performing Hebrew large language model (LLM) presents distinct challenges stemming from the rich and complex nature of the Hebrew language…
Developing a high-performing Hebrew large language model (LLM) presents distinct challenges stemming from the rich and complex nature of the Hebrew language itself. The intricate structure of Hebrew, with words formed through root and pattern combinations, demands sophisticated modeling approaches. Moreover, the lack of capitalization and the frequent absence of punctuation like periods and commas…

 As enterprises adopt generative AI applications powered by large language models (LLMs), there is an increasing need to implement guardrails to ensure safety…
As enterprises adopt generative AI applications powered by large language models (LLMs), there is an increasing need to implement guardrails to ensure safety…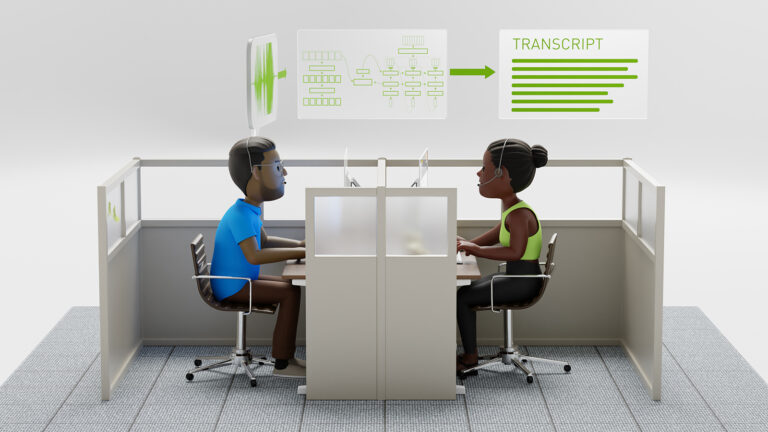 Building an effective automatic speech recognition (ASR) model for underrepresented languages presents unique challenges due to limited data resources. In…
Building an effective automatic speech recognition (ASR) model for underrepresented languages presents unique challenges due to limited data resources. In… Nsight Compute 2024.3 improves selectively exporting results into a new report, kernel name logging to debug empty reports, and profiling green contexts.
Nsight Compute 2024.3 improves selectively exporting results into a new report, kernel name logging to debug empty reports, and profiling green contexts. The exponential growth in data processing demand is projected to reach 175 zettabytes by 2025. This contrasts sharply with the slowing pace of CPU performance…
The exponential growth in data processing demand is projected to reach 175 zettabytes by 2025. This contrasts sharply with the slowing pace of CPU performance… Imagine being able to put your best sales associate in front of every customer for every interaction. Your best sales associate offers product recommendations…
Imagine being able to put your best sales associate in front of every customer for every interaction. Your best sales associate offers product recommendations… The release supports GB100 capabilities and new library enhancements to cuBLAS, cuFFT, cuSOLVER, cuSPARSE, as well as the release of Nsight Compute 2024.3.
The release supports GB100 capabilities and new library enhancements to cuBLAS, cuFFT, cuSOLVER, cuSPARSE, as well as the release of Nsight Compute 2024.3.