 Telecom companies are challenged with consistently meeting service level agreements (SLAs) for end customers that ensure network quality of service. This…
Telecom companies are challenged with consistently meeting service level agreements (SLAs) for end customers that ensure network quality of service. This…
Telecom companies are challenged with consistently meeting service level agreements (SLAs) for end customers that ensure network quality of service. This includes quickly troubleshooting network devices with complex issues, identifying root causes, and resolving issues efficiently at their network operations centers (NOCs). Current network troubleshooting and repair processes are often time…

 Telecom wireless network design demands streamlined processes and standardized approaches. Network architects, engineers, and IT professionals are challenged…
Telecom wireless network design demands streamlined processes and standardized approaches. Network architects, engineers, and IT professionals are challenged… Complimentary trainings on OpenUSD, Digital Humans, LLMs and more with hands-on labs for Full Conference and Experience attendees.
Complimentary trainings on OpenUSD, Digital Humans, LLMs and more with hands-on labs for Full Conference and Experience attendees. An open ecosystem for physics-informed machine learning (physics-ML) fosters innovation and AI engineering applications. Physics-ML embeds into the learning…
An open ecosystem for physics-informed machine learning (physics-ML) fosters innovation and AI engineering applications. Physics-ML embeds into the learning…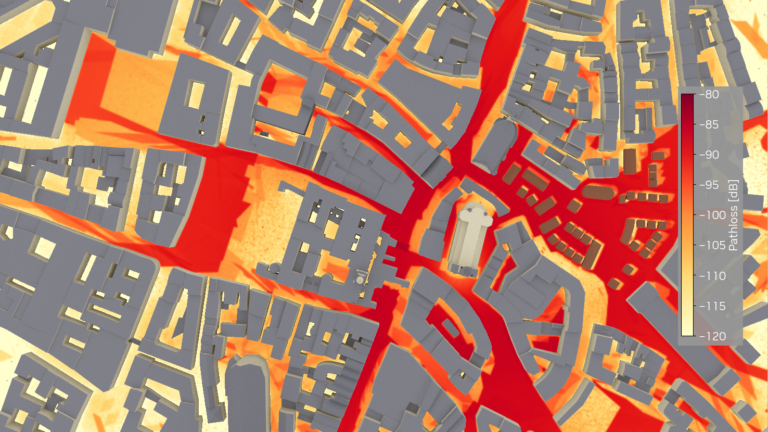 Wireless networks are the essential infrastructure that enables seamless connectivity. To ensure the best performance, whether in a single building or a whole…
Wireless networks are the essential infrastructure that enables seamless connectivity. To ensure the best performance, whether in a single building or a whole…