Businesses seeking to harness the power of AI need customized models tailored to their specific industry needs. NVIDIA AI Foundry is a service that enables enterprises to use data, accelerated computing and software tools to create and deploy custom models that can supercharge their generative AI initiatives. Just as TSMC manufactures chips designed by other
Read Article
 Telecom companies are challenged with consistently meeting service level agreements (SLAs) for end customers that ensure network quality of service. This…
Telecom companies are challenged with consistently meeting service level agreements (SLAs) for end customers that ensure network quality of service. This…
Telecom companies are challenged with consistently meeting service level agreements (SLAs) for end customers that ensure network quality of service. This includes quickly troubleshooting network devices with complex issues, identifying root causes, and resolving issues efficiently at their network operations centers (NOCs). Current network troubleshooting and repair processes are often time…
 Telecom wireless network design demands streamlined processes and standardized approaches. Network architects, engineers, and IT professionals are challenged…
Telecom wireless network design demands streamlined processes and standardized approaches. Network architects, engineers, and IT professionals are challenged…
Telecom wireless network design demands streamlined processes and standardized approaches. Network architects, engineers, and IT professionals are challenged with manually retrieving and customizing Topology and Orchestration Specification for Cloud Applications (TOSCA) templates to meet firm industry specifications. This leads to reduced productivity and increases the risk of human errors and…
Team NVIDIA has triumphed at the Amazon KDD Cup 2024, securing first place Friday across all five competition tracks. The team — consisting of NVIDIANs Ahmet Erdem, Benedikt Schifferer, Chris Deotte, Gilberto Titericz, Ivan Sorokin and Simon Jegou — demonstrated its prowess in generative AI, winning in categories that included text generation, multiple-choice questions, name
Read Article
Gets Hands-On Training at SIGGRAPH 2024
 Complimentary trainings on OpenUSD, Digital Humans, LLMs and more with hands-on labs for Full Conference and Experience attendees.
Complimentary trainings on OpenUSD, Digital Humans, LLMs and more with hands-on labs for Full Conference and Experience attendees.
Complimentary trainings on OpenUSD, Digital Humans, LLMs and more with hands-on labs for Full Conference and Experience attendees.
 An open ecosystem for physics-informed machine learning (physics-ML) fosters innovation and AI engineering applications. Physics-ML embeds into the learning…
An open ecosystem for physics-informed machine learning (physics-ML) fosters innovation and AI engineering applications. Physics-ML embeds into the learning…
An open ecosystem for physics-informed machine learning (physics-ML) fosters innovation and AI engineering applications. Physics-ML embeds into the learning process the knowledge of physical laws that govern a given dataset. This enables scientists to use prior knowledge to help train a neural network, making it more generalizable and efficient. Yet, as physics-ML is a growing field of…
WWDC 24: Running Mistral 7B with Core ML
AI and accelerated computing — twin engines NVIDIA continuously improves — are delivering energy efficiency for many industries. It’s progress the wider community is starting to acknowledge. “Even if the predictions that data centers will soon account for 4% of global energy consumption become a reality, AI is having a major impact on reducing the
Read Article
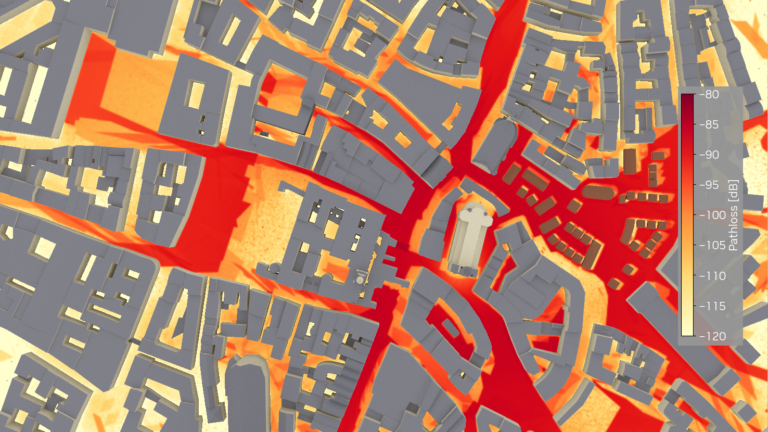 Wireless networks are the essential infrastructure that enables seamless connectivity. To ensure the best performance, whether in a single building or a whole…
Wireless networks are the essential infrastructure that enables seamless connectivity. To ensure the best performance, whether in a single building or a whole…
Wireless networks are the essential infrastructure that enables seamless connectivity. To ensure the best performance, whether in a single building or a whole city, such networks are optimized using radio maps, which show the received signal strength across a large area, among other information. Until now, the creation of radio maps was believed to be time-consuming, limiting the utility of…
