 As cyberattacks become more sophisticated, organizations must constantly adapt with cutting-edge solutions to protect their critical assets. One such solution…
As cyberattacks become more sophisticated, organizations must constantly adapt with cutting-edge solutions to protect their critical assets. One such solution…
As cyberattacks become more sophisticated, organizations must constantly adapt with cutting-edge solutions to protect their critical assets. One such solution is Cisco Secure Workload, a comprehensive security solution designed to safeguard application workloads across diverse infrastructures, locations, and form factors. Cisco recently announced version 3.9 of the Cisco Secure Workload…

 Join the webinar on June 11th with NVIDIA and Super Protocol to learn about the benefits of Confidential Computing for Web3 AI.
Join the webinar on June 11th with NVIDIA and Super Protocol to learn about the benefits of Confidential Computing for Web3 AI. In today’s digital age, creating realistic animated characters is crucial for filmmakers, game developers, and content creators looking to bring their visions…
In today’s digital age, creating realistic animated characters is crucial for filmmakers, game developers, and content creators looking to bring their visions… Create high-resolution images with remarkable efficiency with the Advanced text-to-image generation model, SDXL-Lightning, available and optimized now on the…
Create high-resolution images with remarkable efficiency with the Advanced text-to-image generation model, SDXL-Lightning, available and optimized now on the… Enhance efficiency and performance in instruction-based NLP tasks with SOLAR-10.7B, especially in following instructions, reasoning, and mathematical tasks.
Enhance efficiency and performance in instruction-based NLP tasks with SOLAR-10.7B, especially in following instructions, reasoning, and mathematical tasks. The latest embedding model from NVIDIA—NV-Embed—set a new record for embedding accuracy with a score of 69.32 on the Massive Text Embedding Benchmark…
The latest embedding model from NVIDIA—NV-Embed—set a new record for embedding accuracy with a score of 69.32 on the Massive Text Embedding Benchmark… Generative AI enables users to quickly generate new content based on a variety of inputs. Inputs and outputs to these models can include text, images, sounds,…
Generative AI enables users to quickly generate new content based on a variety of inputs. Inputs and outputs to these models can include text, images, sounds,… The latest state-of-the-art foundation large language models (LLMs) have billions of parameters and are pretrained on trillions of tokens of input text. They…
The latest state-of-the-art foundation large language models (LLMs) have billions of parameters and are pretrained on trillions of tokens of input text. They…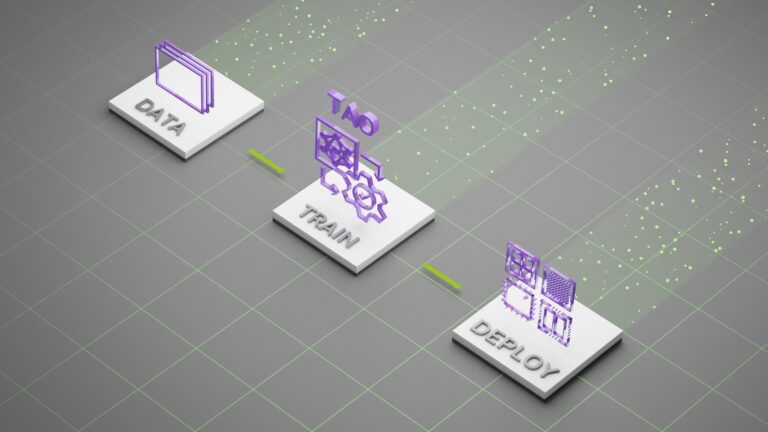 MediaTek is teaming with NVIDIA to integrate NVIDIA TAO training and pretrained models into its development workflow, bringing advanced AI and visual perception…
MediaTek is teaming with NVIDIA to integrate NVIDIA TAO training and pretrained models into its development workflow, bringing advanced AI and visual perception…