NVIDIA today announced that it will accelerate quantum computing efforts at national supercomputing centers around the world with the open-source NVIDIA CUDA-Q™ platform.
Data centers need an upgraded dashboard to guide their journey to greater energy efficiency, one that shows progress running real-world applications. The formula for energy efficiency is simple: work done divided by energy used. Applying it to data centers calls for unpacking some details. Today’s most widely used gauge — power usage effectiveness (PUE) —
Read Article
Generative AI is taking root at national and corporate labs, accelerating high-performance computing for business and science. Researchers at Sandia National Laboratories aim to automatically generate code in Kokkos, a parallel programming language designed for use across many of the world’s largest supercomputers. It’s an ambitious effort. The specialized language, developed by researchers from several
Read Article
Quantum computing. Drug discovery. Fusion energy. Scientific computing and physics-based simulations are poised to make giant steps across domains that benefit humanity as advances in accelerated computing and AI drive the world’s next big breakthroughs. NVIDIA unveiled at GTC in March the NVIDIA Blackwell platform, which promises generative AI on trillion-parameter large language models (LLMs)
Read Article
 In the rapidly evolving field of software development, AI tools such as chatbots and GitHub Copilot have significantly transformed how developers write and…
In the rapidly evolving field of software development, AI tools such as chatbots and GitHub Copilot have significantly transformed how developers write and…
Enabling Quantum Computing with AI
 Building a useful quantum computer in practice is incredibly challenging. Significant improvements are needed in the scale, fidelity, speed, reliability, and…
Building a useful quantum computer in practice is incredibly challenging. Significant improvements are needed in the scale, fidelity, speed, reliability, and…
Building a useful quantum computer in practice is incredibly challenging. Significant improvements are needed in the scale, fidelity, speed, reliability, and programmability of quantum computers to fully realize their benefits. Powerful tools are needed to help with the many complex physics and engineering challenges that stand in the way of useful quantum computing.
 NVIDIA CUDA-Q (formally NVIDIA CUDA Quantum) is an open-source programming model for building quantum accelerated supercomputing applications that take full…
NVIDIA CUDA-Q (formally NVIDIA CUDA Quantum) is an open-source programming model for building quantum accelerated supercomputing applications that take full…
NVIDIA CUDA-Q (formally NVIDIA CUDA Quantum) is an open-source programming model for building quantum accelerated supercomputing applications that take full advantage of CPU, GPU, and QPU compute abilities. Developing these applications today is challenging and requires an easy-to-use coding environment coupled with powerful quantum simulation capabilities to efficiently evaluate and improve the…
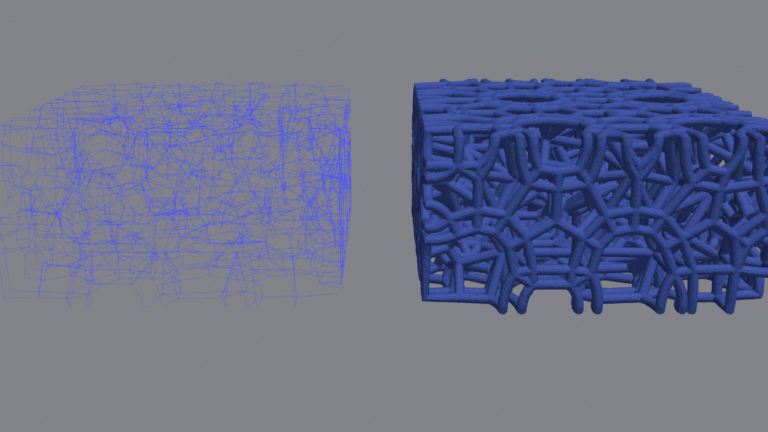 Lattice structures are naturally and artificially made designs that are important in many scientific fields, such as materials science, aerospace engineering,…
Lattice structures are naturally and artificially made designs that are important in many scientific fields, such as materials science, aerospace engineering,…
Lattice structures are naturally and artificially made designs that are important in many scientific fields, such as materials science, aerospace engineering, and biomedical engineering. They are made by repeating patterns that connect smaller truss structures and yield a high strength-to-weight ratio. The rise of 3D printing within additive manufacturing has highlighted the significance of…
 CUDA Graphs can provide a significant performance increase, as the driver is able to optimize execution using the complete description of tasks and…
CUDA Graphs can provide a significant performance increase, as the driver is able to optimize execution using the complete description of tasks and…
CUDA Graphs can provide a significant performance increase, as the driver is able to optimize execution using the complete description of tasks and dependencies. Graphs provide incredible benefits for static workflows where the overhead of graph creation can be amortized over many successive launches. However, nearly all problems involve some form of decision-making…
Explainer: What Is Artificial Intelligence?
 In its most fundamental form, AI is the capability of a computer program or a machine to think, learn, and take action without being explicitly encoded with…
In its most fundamental form, AI is the capability of a computer program or a machine to think, learn, and take action without being explicitly encoded with…
In its most fundamental form, AI is the capability of a computer program or a machine to think, learn, and take action without being explicitly encoded with commands.
