Large language models (LLMs) are reshaping productivity. They’re capable of drafting documents, summarizing web pages and, having been trained on vast quantities of data, accurately answering questions about nearly any topic.
 In the field of automotive vehicle software development, more large-scale AI models are being integrated into autonomous vehicles. The models range from vision…
In the field of automotive vehicle software development, more large-scale AI models are being integrated into autonomous vehicles. The models range from vision…
In the field of automotive vehicle software development, more large-scale AI models are being integrated into autonomous vehicles. The models range from vision AI models to end-to-end AI models for autonomous driving. Now the demand for computing power is sharply increasing, leading to higher system loads that can have a negative impact on system stability and latency.
NVIDIA founder and CEO Jensen Huang joined the king of Denmark to launch the country’s largest sovereign AI supercomputer, aimed at breakthroughs in quantum computing, clean energy, biotechnology and other areas serving Danish society and the world. Denmark’s first AI supercomputer, named Gefion after a goddess in Danish mythology, is an NVIDIA DGX SuperPOD driven
Read Article
Deploying Speech-to-Speech on Hugging Face
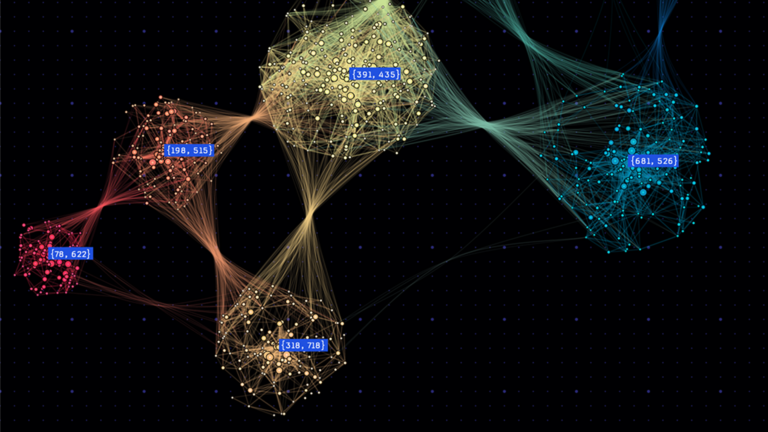 NetworkX accelerated by NVIDIA cuGraph is a newly released backend co-developed with the NetworkX team. NVIDIA cuGraph provides GPU acceleration for popular…
NetworkX accelerated by NVIDIA cuGraph is a newly released backend co-developed with the NetworkX team. NVIDIA cuGraph provides GPU acceleration for popular…
NetworkX accelerated by NVIDIA cuGraph is a newly released backend co-developed with the NetworkX team. NVIDIA cuGraph provides GPU acceleration for popular graph algorithms such as PageRank, Louvain, and betweenness centrality. Depending on the algorithm and graph size, it can significantly accelerate NetworkX workflows, up to 50x, even 500x over NetworkX on CPU. In this post…
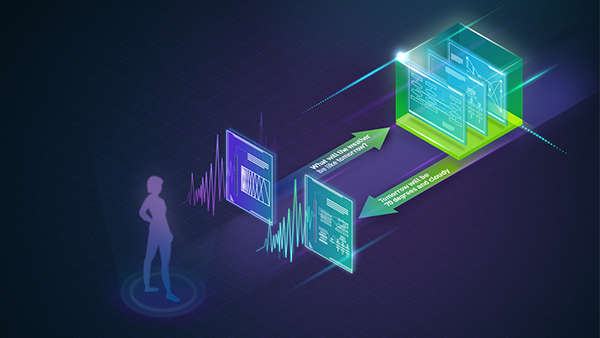 The Automated Audio Captioning task centers around generating natural language descriptions from audio inputs. Given the distinct modalities between the input…
The Automated Audio Captioning task centers around generating natural language descriptions from audio inputs. Given the distinct modalities between the input…
The Automated Audio Captioning task centers around generating natural language descriptions from audio inputs. Given the distinct modalities between the input (audio) and the output (text), AAC systems typically rely on an audio encoder to extract relevant information from the sound, represented as feature vectors, which a decoder then uses to generate text descriptions.
 Large language models (LLMs) have been widely used for chatbots, content generation, summarization, classification, translation, and more. State-of-the-art LLMs…
Large language models (LLMs) have been widely used for chatbots, content generation, summarization, classification, translation, and more. State-of-the-art LLMs…
Large language models (LLMs) have been widely used for chatbots, content generation, summarization, classification, translation, and more. State-of-the-art LLMs and foundation models, such as Llama, Gemma, GPT, and Nemotron, have demonstrated human-like understanding and generative abilities. Thanks to these models, AI developers do not need to go through the expensive and time consuming training…
